DLP policies are used in the following contexts for core Microsoft 365 workloads:
• Exchange Online: Apply controls or restrictions to messages as they are sent or received by individuals in the organization.
• SharePoint Online and OneDrive for Business: Restrict sensitive content as it is added to a sharing invitation.
• Teams: Restrict sensitive content as it is entered into a chat or channel message.
• Devices: Protect content on endpoint devices. This option requires additional configuration.
• On-premises file servers: Protect content in connected on-premises repositories. This option requires additional configuration.
To configure a workload DLP policy, follow these steps:
- Navigate to the Microsoft Purview compliance portal (https://compliance.microsoft. com).
- Under Solutions, expand Data loss prevention and then select Policies.
- Click Create policy. See Figure 11.1:
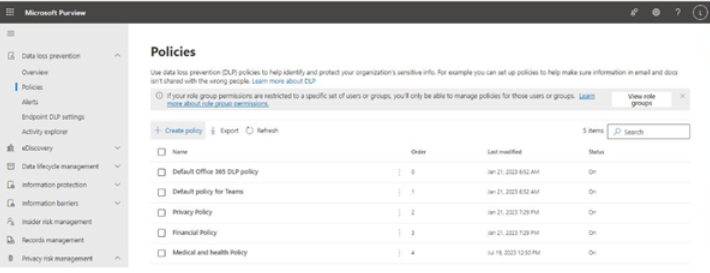
Figure 11.1 – Microsoft Purview compliance policies page
- Choose whether to use one of the built-in templates or to create a new custom policy.
Built-in templates are broken into categories such as Enhanced (various international legislation, finance, or privacy regulations, which utilize trainable classifiers to extend detection capabilities), Financial (international financial data types), Medical and health (healthcare legislation, terms, and personal information), and Privacy (international privacy regulations or legislation). You can only choose one template; if you want to include more than one template data type, you’ll need to select Custom and add the sensitive information types or other classifiers manually.
- Click Next when the policy type has been selected. See Figure 11.2:
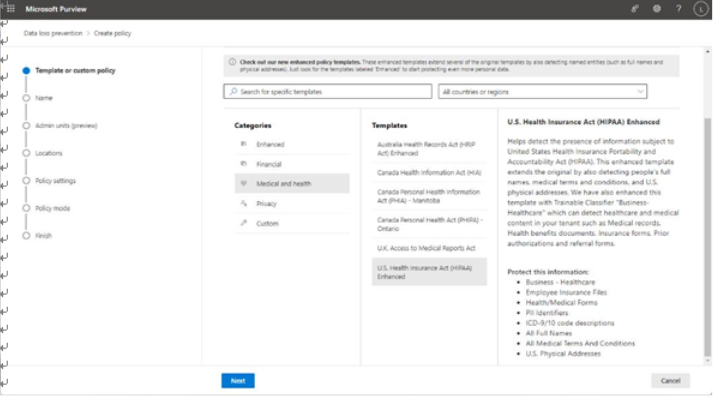
Figure 11.2 – Selecting a template or policy type
- On the Name page, enter a value to identify your policy. Click Next.
- On the Admin units page, as shown in Figure 11.3, choose whether the DLP policy will apply to the whole organization or only to members of a particular administrative unit.
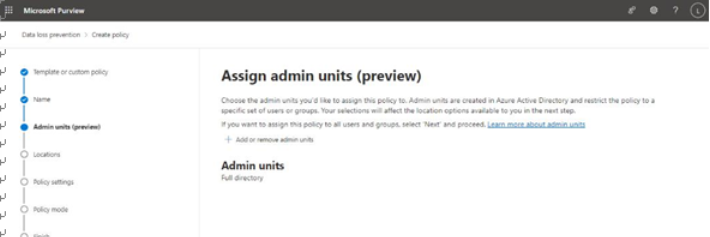
Figure 11.3 – Assigning an administrative unit
Click Next when you’re finished.
- On the Locations page, as shown in Figure 11.4, choose which workloads and locations the policy will be applied to. You can enable all workloads and locations as part of a single policy, with the exception of Power BI. While you can enable devices and on-premises repositories now, those locations will require additional steps to fully onboard and protect. Also, if you are using a new enhanced DLP template for your policy, on-premises repositories aren’t supported.
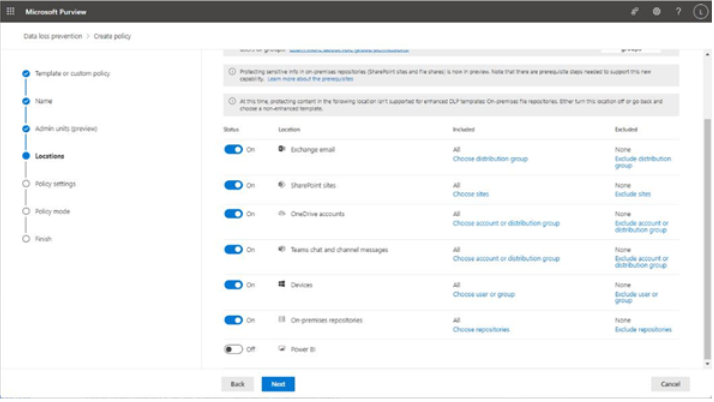
Figure 11.4 – Adding workloads and locations to the policy
For each location, you can apply filters to include or exclude objects (such as users, groups, sites, or devices). When finished, click Next.
- On the Policy settings page, determine what DLP rules you want to apply. You could choose from Review and customize the default settings from the template or Create or customize advanced DLP rules. They both have similar capabilities, though the Create or customize advanced DLP rules option has more flexibility in creating conditions with a more complex editing interface. In this example, you’ll just choose the Review and customize the default settings from the template option, though we’d recommend experimenting with both so you can see the flexibility of the options. Click Next.
- On the Info to protect subpage, as shown in Figure 11.5, select Edit to modify the DLP rule conditions:
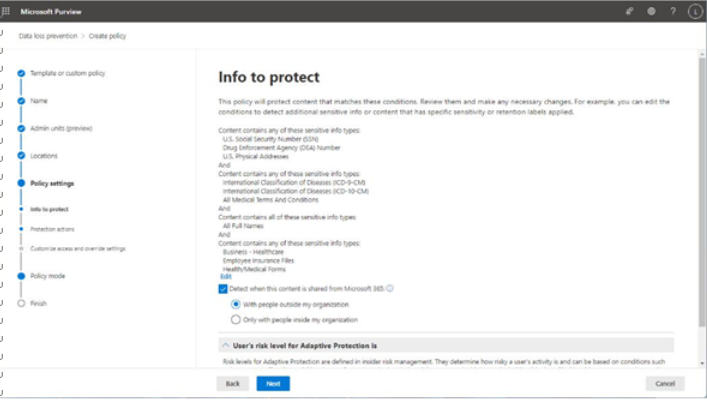
Figure 11.5 – Reviewing the Info to protect page
Exam Tip
If you have selected the Devices or On-premises repositories location, you will not see or be able to select the Detect when this content is shared from Microsoft 365option. If you have selected SharePoint or OneDrive locations, you will not be able to see or use the User’s risk level for Adaptive protection is control. You’ll have to evaluate what features you need to use and potentially create separate policies to protect data in different locations with different features.