The auto-labeling policies, like other content automation policies in Microsoft Purview, use detection algorithms and processes (such as sensitive information types and trainable classifiers) to apply labels to content in the M365 environment. These are service-side labeling features. After you’ve laid out a labeling scheme consisting of labels and sublabels and decided how content should be classified, you can use and customize the templates in the auto-labeling wizard to apply labels to content matching your classifiers.
Suppose, for example, you need to identify and classify documents that have sensitive information, such as U.S. taxpayer identification numbers or social security numbers, and have created a label called Highly Confidential. You can use an auto-labeling policy with one of the predefined templates to detect taxpayer and social security number patterns and then apply a label to those matching documents.
To create an auto-labeling policy, follow these steps:
- In the Microsoft Purview compliance portal (https://compliance.microsoft.com), expand Information protection and select Auto-labeling.
- Click Create auto-labeling policy, as shown in Figure 10.51.
Figure 10.51 – Selecting Create auto-labeling policy
- On the Info to label page, select the template that you want to use to detect sensitive data. You can choose from a variety of sensitive information types including financial, medical, and privacy continuum. You can select Custom to create a policy based on your own criteria and sensitive information types. In this example, the U.S. State Breach Notification Laws Enhanced template has been selected, which includes detections for a number of personal data elements including financial information, taxpayer data, government identification (such as passports and driver’s licenses), and medical terminology.
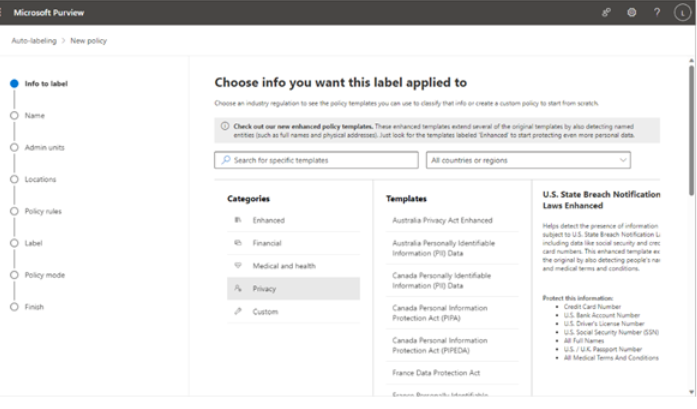
Figure 10.52 – Selecting a category template
- Click Next.
- Enter a Name value for the policy and click Next.
- On the Admin units page, choose which administrative units to use for scoping the policy. By default, the entire tenant is selected. Click Next.
- On the Locations page, choose where you want this policy to apply labels. By default, all Exchange email, SharePoint sites, and OneDrive accounts are selected as part of the application scope. Click Next.
- On the Policy rules page, you can select either Common rules or Advanced rules. Both Common rules and Advanced rules start off with a base template that you can customize, though Advanced rules gives you more customization ability when it comes to email conditions. Select a rules option and click Next.
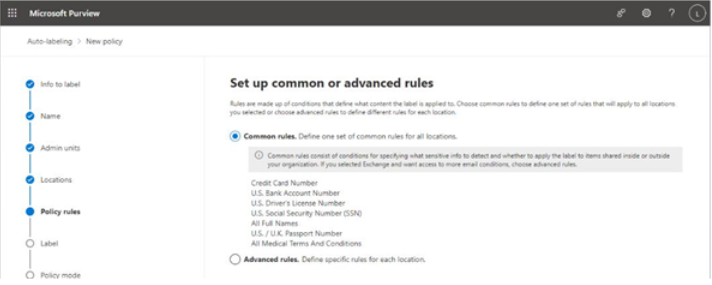
Figure 10.53 – Selecting policy rules
- Review the rules that are in place, customize if desired, and click Next to continue.
- On the Label page, select which label you want to apply to the detected content. Click Next.
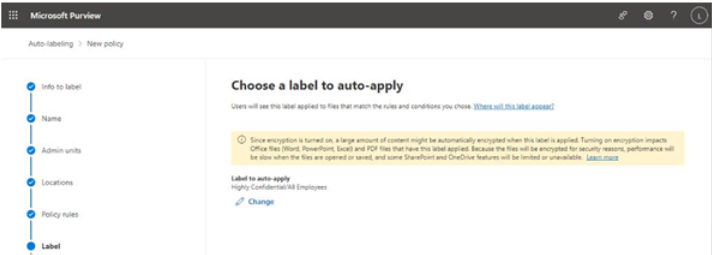
Figure 10.54 – Selecting the label to apply
- If you have Exchange email selected as a location on the Locations page, you have an Automatically replace existing labels that have the same or lower priority option. Additionally, if the label you selected has encryption settings, you can choose Apply encryption to email received from outside of the organization if required. If you do not choose Assign a Rights Management owner, encryption will not be applied to received emails.
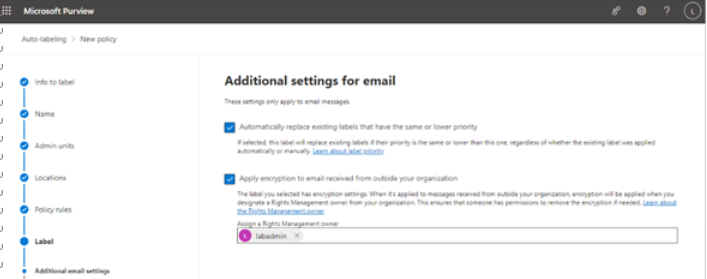
Figure 10.55 – Specifying additional settings for email
- Click Next.
- On the Policy mode page, select how the policy will be implemented. There is no setting to turn the policy on immediately, though you can choose Run the policy in simulation mode and then select the Automatically turn on policy if not modified after 7 days in simulation option. You can also choose Leave policy turned off if you’re not ready to move forward with it just yet.
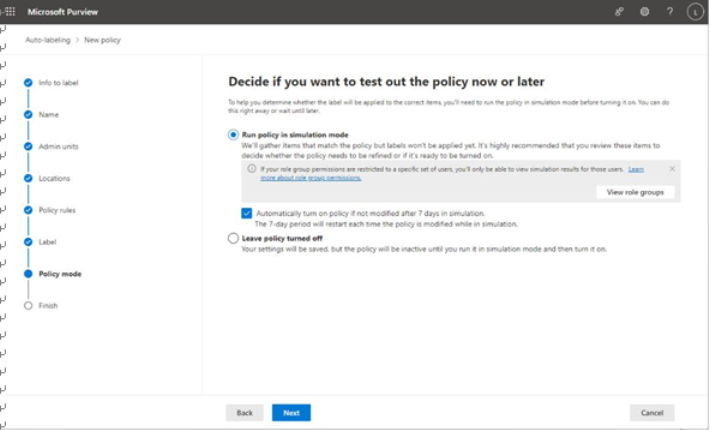
Figure 10.56 – Choosing the policy mode
- Click Next.
- On the Finish page, review the settings and adjust if necessary. Click Create policy.
A labeling policy (whether a standard label policy or an auto-label policy) can only apply a single label to content. Additionally, an item may only have one sensitivity label applied to it at a time. If you have multiple labels and sublabels and want to automatically apply multiple labels, you’ll need to create a separate policy for each label that you want to apply. Labels also have a concept of priority— where a higher number means it has a higher priority. If a labeling policy identifies content that could potentially match two labels with different priorities, M365 will apply the label with the higher priority to the content.
Exam tip
The core takeaway from the two types of labeling policies is that label policies are generally focused on interactive activities (such as navigating a browser interface to apply a label or applying a label while creating and editing a document) while auto-labeling policies generally apply to content at rest.