While many cloud-based applications and services may use their own identity stores, it is becoming more common for application vendors to allow bring-you-own-identity scenarios. You might see this with websites allowing social media logins or other types of identity.
Like other identity providers, Azure AD identity can be used to authenticate users to external applications. While many of those applications are legitimate (and their use derives from a legitimate business use case), malicious websites or individuals can publish applications to steal data. As part of your operational practices, you should periodically review allowed applications in your environment and remove the authorizations for applications that look suspicious or are no longer being used.
Applications that are registered or authorized in Azure AD can be used to provide single sign-on to both SaaS cloud applications as well as internally managed applications. Depending on your organization’s settings, applications may be authorized by end users, administrators, or both.
There are several things you can do to monitor application access:
- Create and manage access reviews
- Review audit logs
- Review the sign-ins report
- Send activity log data to Azure Monitor
Let’s look at each of these areas briefly.
Creating and managing access reviews
The primary goal of an access review is to confirm that those who have access to an application or other resource still have access. If a user, whether internal or external, no longer requires the ability to use a resource, their access to that resource should be terminated.
Note
Access reviews are a feature of Identity Governance and require Azure AD Premium P2.
To create an access review, follow these steps:
- Log in to the Azure portal (https://portal.azure.com) with a user that has one of the prerequisite role assignments (Global Administrator, User Administrator, Identity Governance Administrator, or Privileged Role Administrator) or who is an owner of the group for which the access review will be created.
- In the search box, enter Identity Governance and select the Identity Governance item.
- Under the Access reviews navigation menu item, select Access reviews:
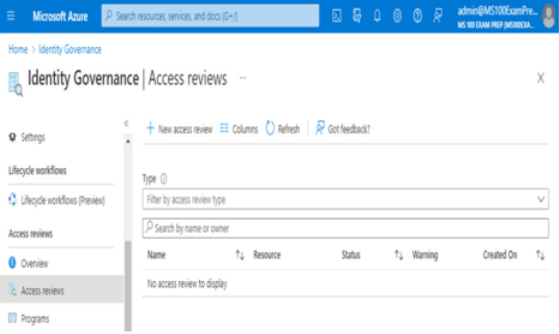
Figure 2.9 – Access reviews
- Select + New access review.
- In the Select Review dropdown, select Teams + Groups or Applications:
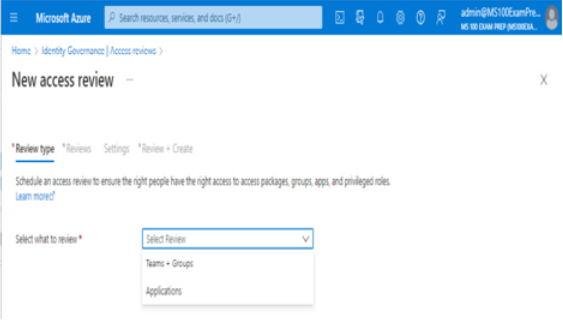
Figure 2.10 – New access review – the Select Review dropdown
- Depending on your selection, choose from All Microsoft 365 groups with guest users, Select Teams + groups (if you choose the Teams + Groups option), or one or more registered applications (if you choose the Applications option). If you select Teams + Groups, you may have additional selections regarding specific groups to include or exclude or specific scopes of users to include or exclude.
- Click Next.
- Under Specify reviewers, select the individuals who will be responsible for auditing the group. You may be asked to provide Fallback reviewers (if the ones you initially select cease to exist in the future), depending on the options you select.
- Depending on your settings, you may see an option to perform a multi-stage review. Multi-stage reviews allow you to add up to three stages of reviewers to audit the membership of a group.
- Under Specify recurrence of review, set a Duration (in days) period, a Review recurrence option (one-time, weekly, monthly, quarterly, semi-annually, or annually), and start and end date parameters. Click Next.
- Under Upon completion settings, choose whether to Auto apply results to a resource and what to do If reviewers don’t respond:
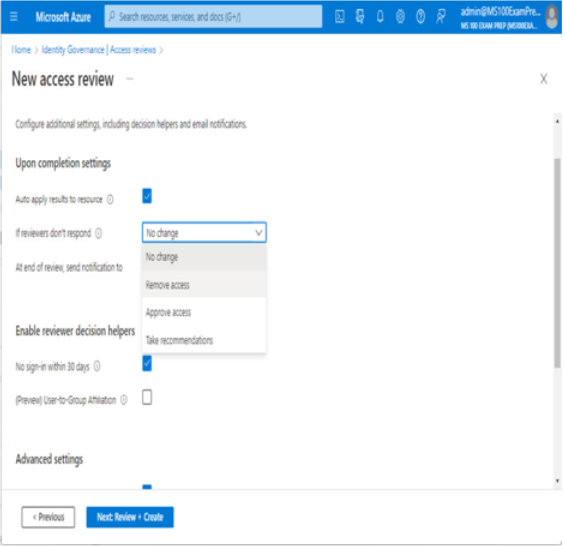
Figure 2.11 – Access review additional settings
- You can also choose to Enable reviewer decision helpers, which are like tooltips that provide additional information on the selected actions during the access review.
- Under Advanced settings, you can choose additional options such as Justification required, enable Email notifications and Reminders to complete access reviews, and use a text box to specify Additional context for reviewer email, which can be used to further explain the access review process to the individuals you’ve selected.
- Click Next.
- Enter a name for the access review, review the configured options, and then click Create to create your access review.
After an access review has been created, Azure AD will evaluate whether it needs to run. If the workflow determines it is time for the access review to run, it will do so.
You can view the status of an access review by clicking on it on the Identity governance | Access reviews page.
Users who have been selected to be reviewers will receive an email notification with a link to the access review page. You can also view the access review by selecting Results under the Manage menu item. From there, you’ll be able to view the recommended actions and the audit information for review:
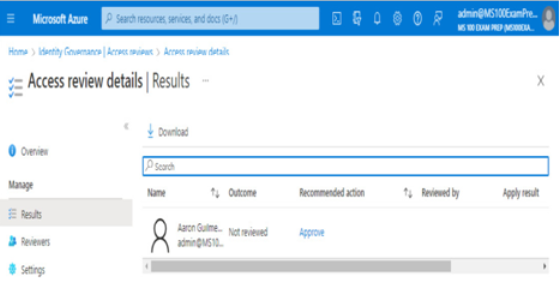
Figure 2.12 – Access review results
Next, we’ll look at some of the logging and reporting data available for applications.