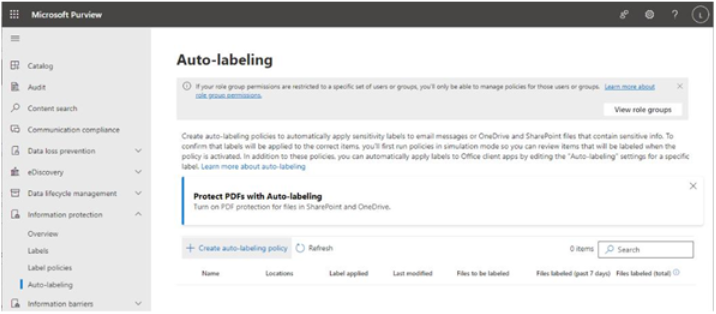
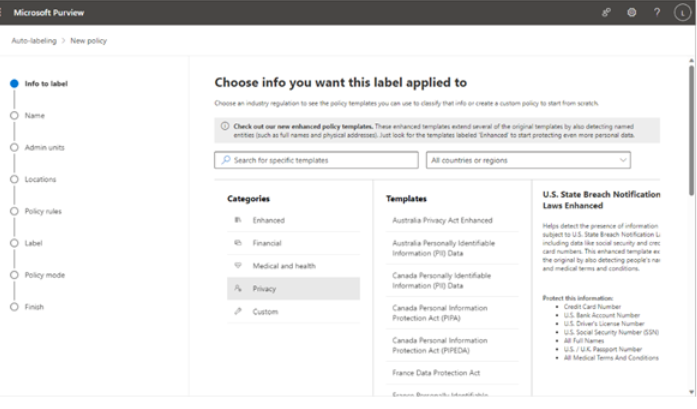
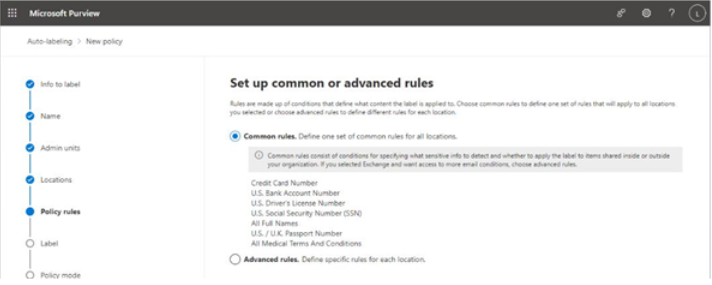
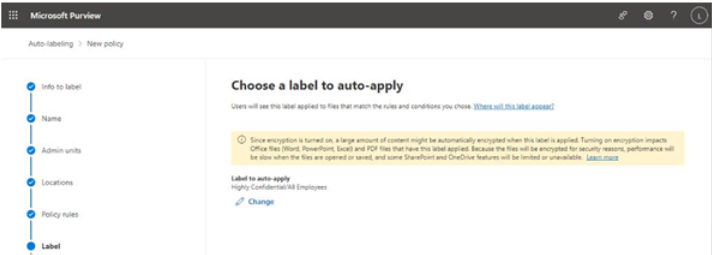
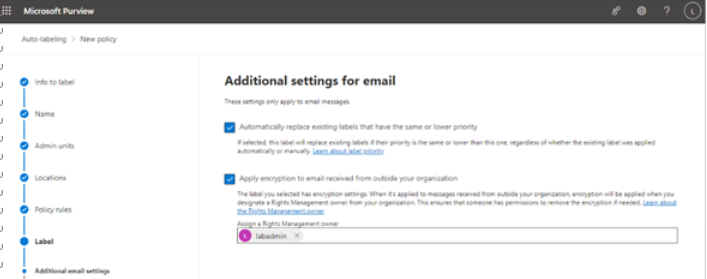
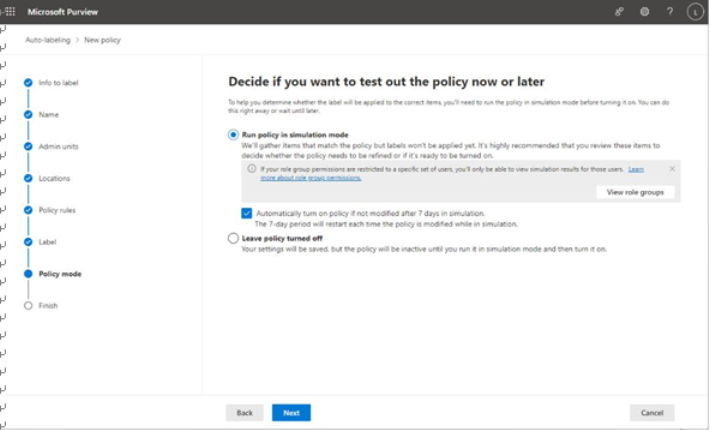
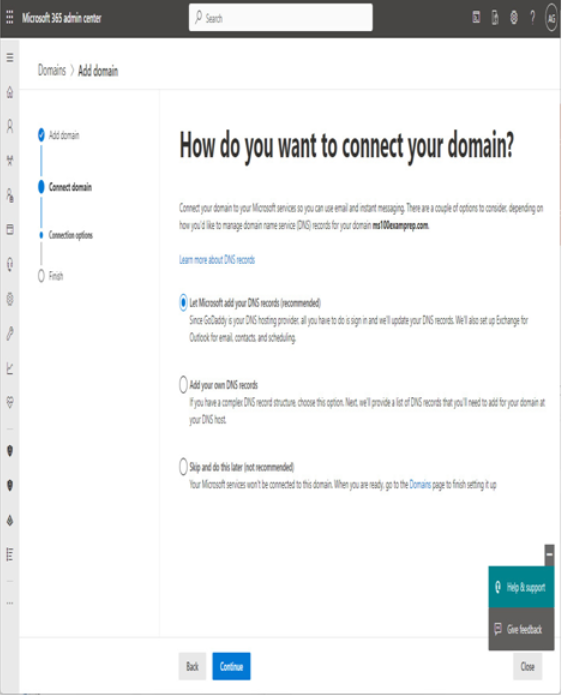
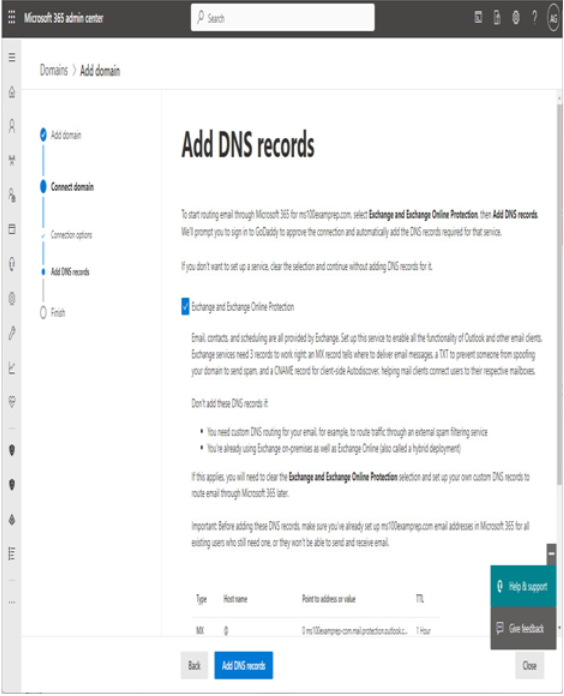
There are a number of early planning stages for a Microsoft 365 tenant, but the one you’re presented with first will be which kind of subscription and tenant you acquire. Tenants and subscriptions are available for different sizes of organizations as well as different industry verticals. Depending on what options you choose, you may not be able to easily change plans without performing a migration (for example, when moving between Microsoft 365 Commercial and Microsoft 365 GCC).
Selecting a tenant type
Microsoft has made a variety of packages available, targeting different types of organizations, as shown in Figure 1.1:
Figure 1.1 – Types of tenants
Tenant type deep dive
The MS-100 exam focuses on the feature set and product or service bundles available in Microsoft 365 Enterprise plans, though the technologies available are largely the same across all plans. Microsoft 365 for US Government is available only for local, state, and federal government customers (and their partners or suppliers) and has a subset of the currently commercially available features, trailing by anywhere from 6 months to 2 years, depending on the certification level of the environment. Microsoft 365 for Education has the same feature set as the commercial enterprise set, with a few added features targeted to educational institutions. Microsoft 365 for Education is only available to schools and universities.
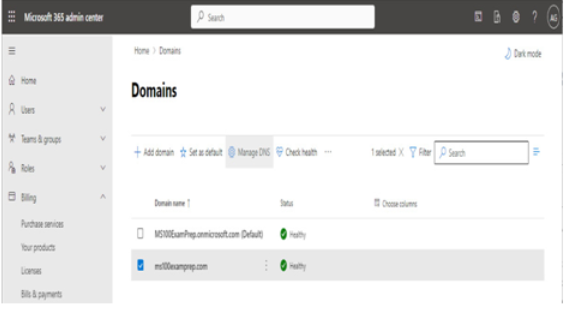
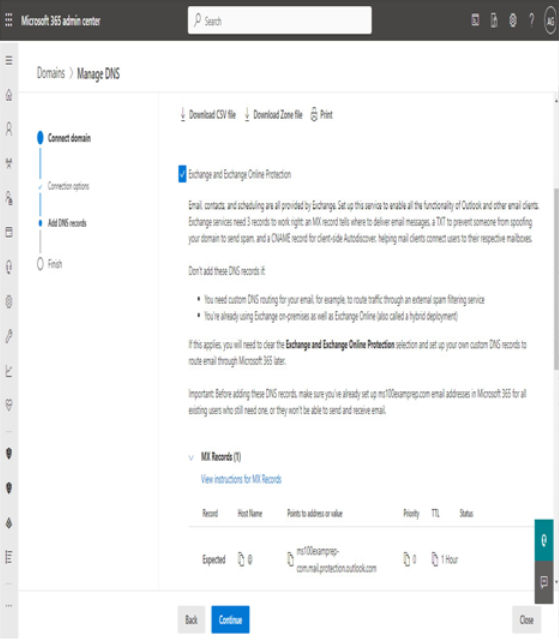
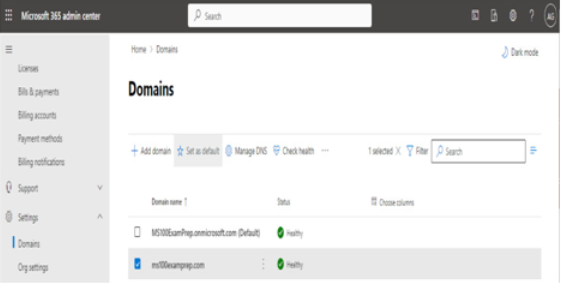
Selecting a managed domain
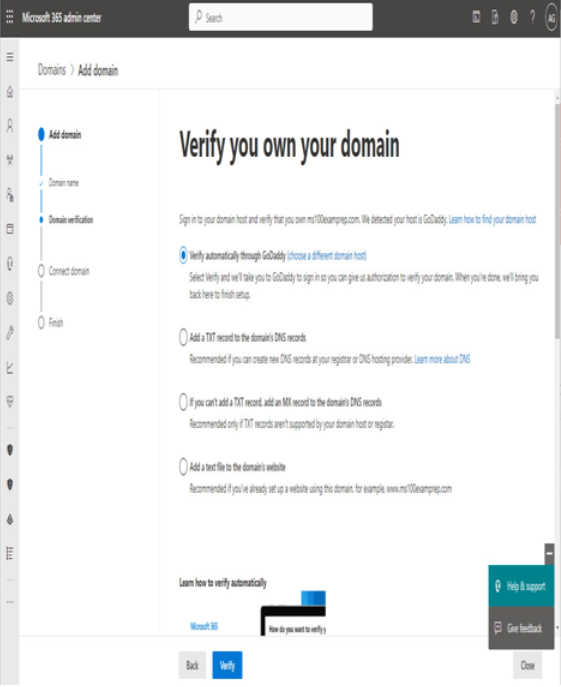
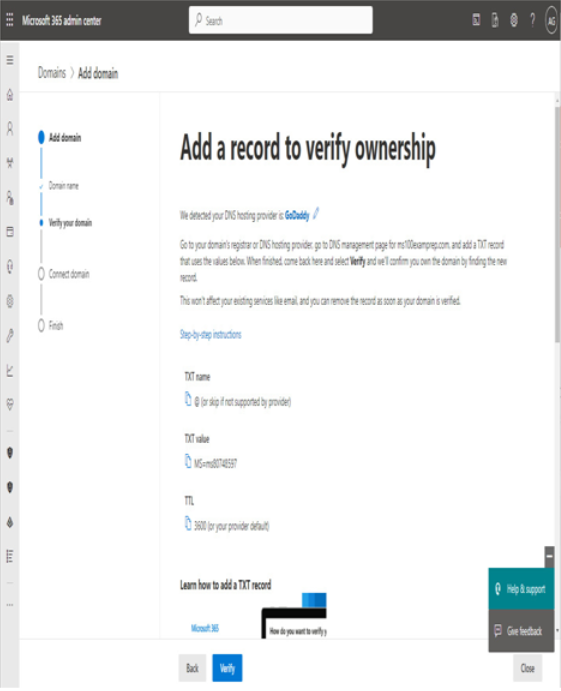
After choosing what type of subscription and tenant you’ll acquire, one of the next steps you’ll be faced with is naming your tenant. When you sign up for a Microsoft 365 subscription, you are prompted to choose a name in the Microsoft onmicrosoft.com managed namespace. The name you select will need to be unique across all other Microsoft 365 customers.
Tenant name considerations
The tenant name (or managed domain name) cannot be changed after it has been selected. As such, it’s important to select one that is appropriate for your organization. The tenant name is visible in a handful of locations, so be sure to select a name that doesn’t reveal any private information and looks professionally appropriate for the type of organization you’re representing.