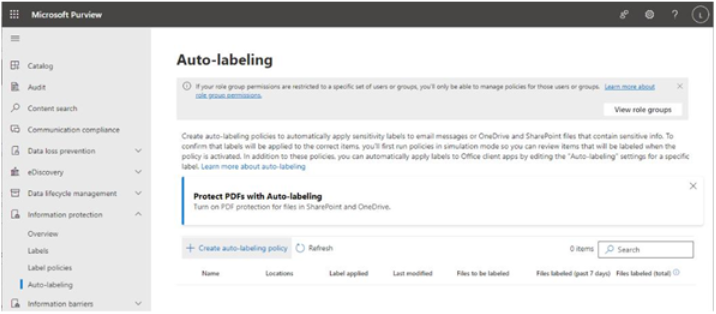
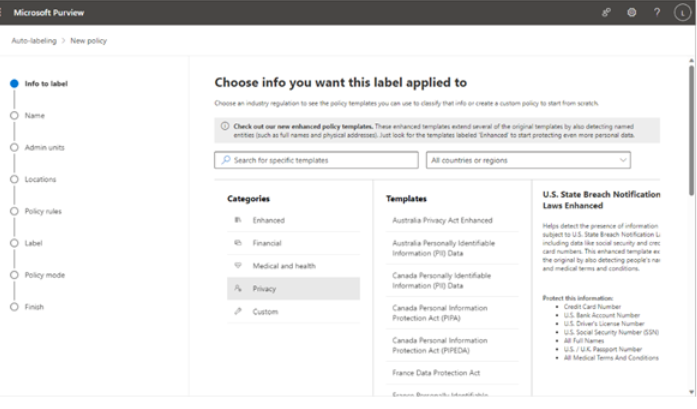
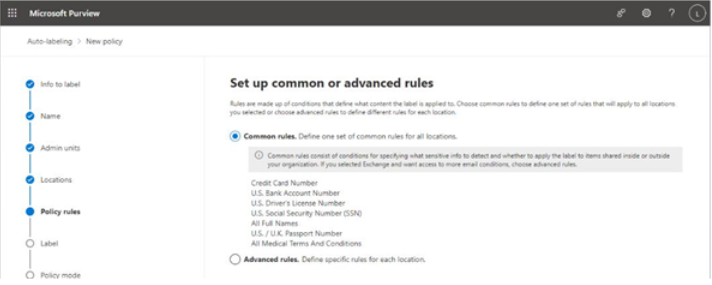
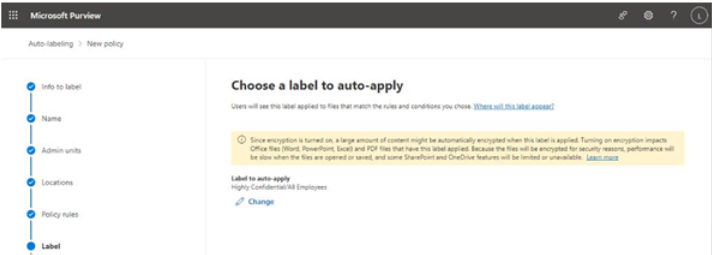
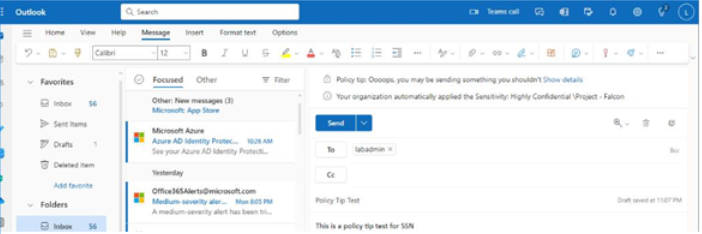
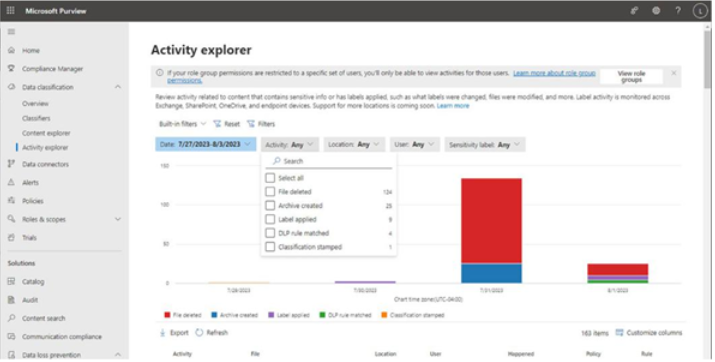
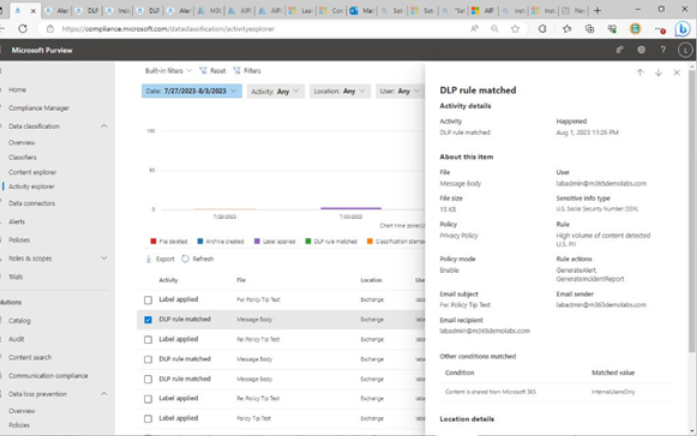
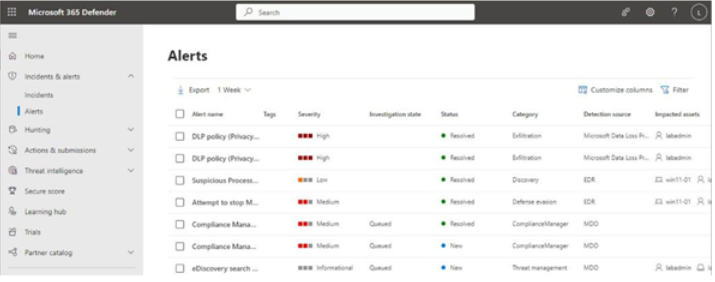
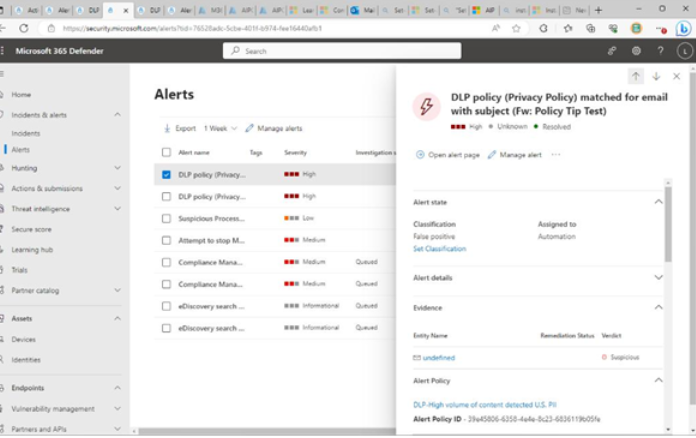
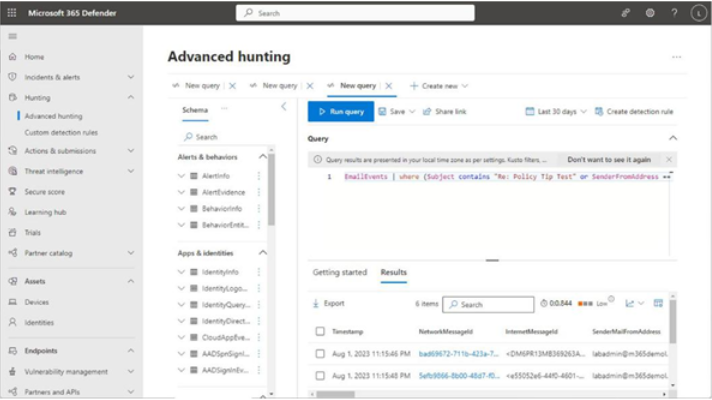
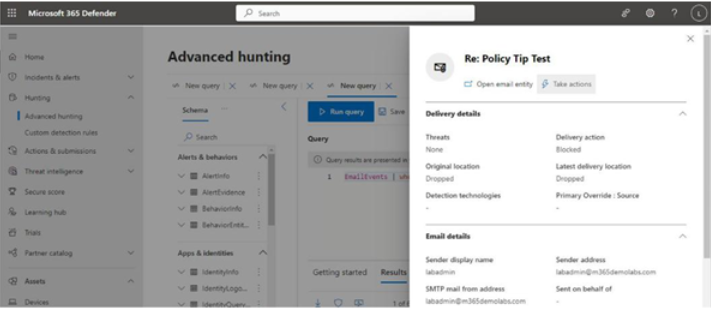
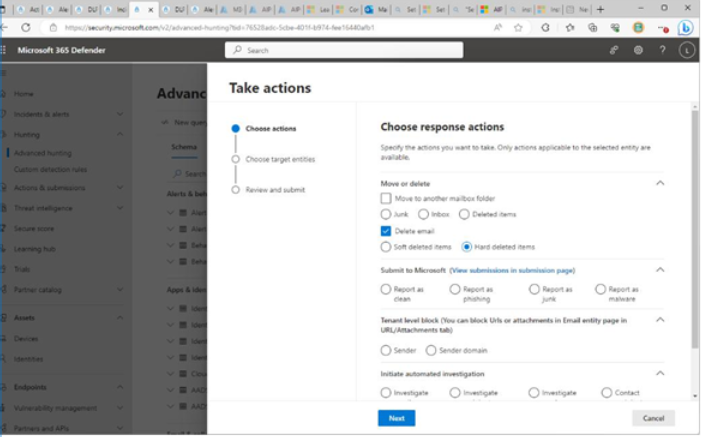
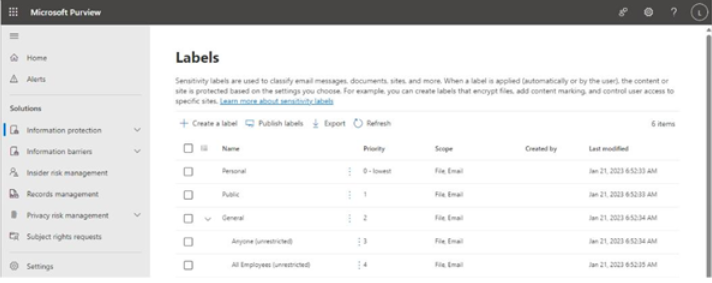
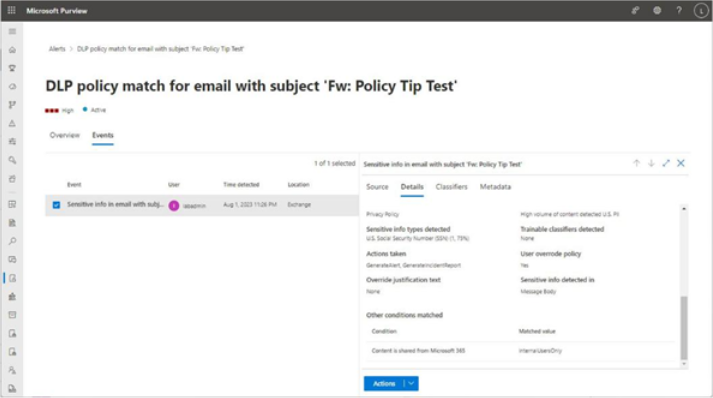
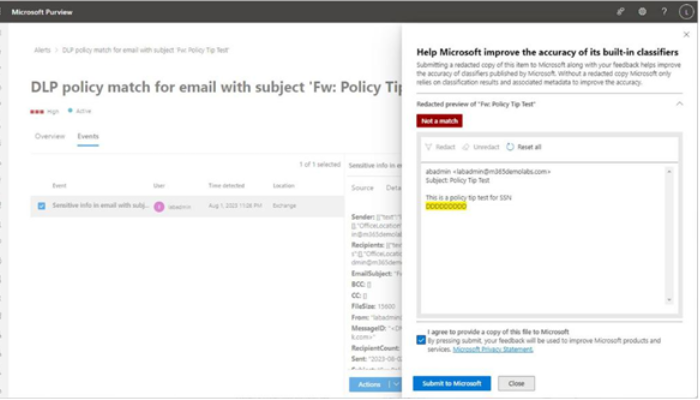
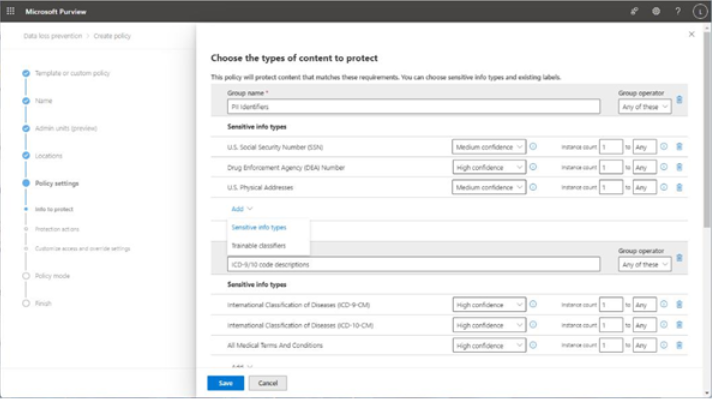
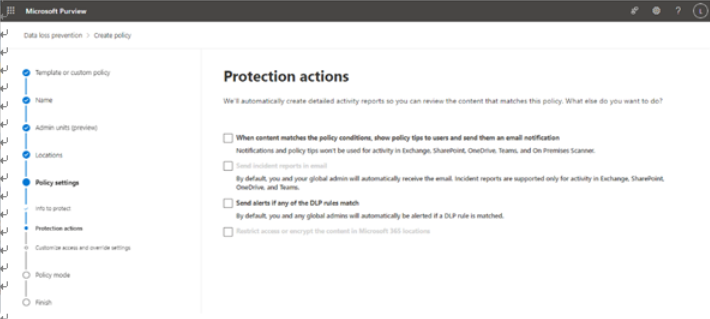
The Microsoft 365 usage reports are available inside the Microsoft 365 admin center. They are broad reports that can be used to get a high-level snapshot of how your organization uses the Microsoft 365 platform. Report data includes statistics about how many files are stored in SharePoint, how many Exchange mailboxes were active during the reporting period, as well as engagement with other products such as Yammer or Forms:
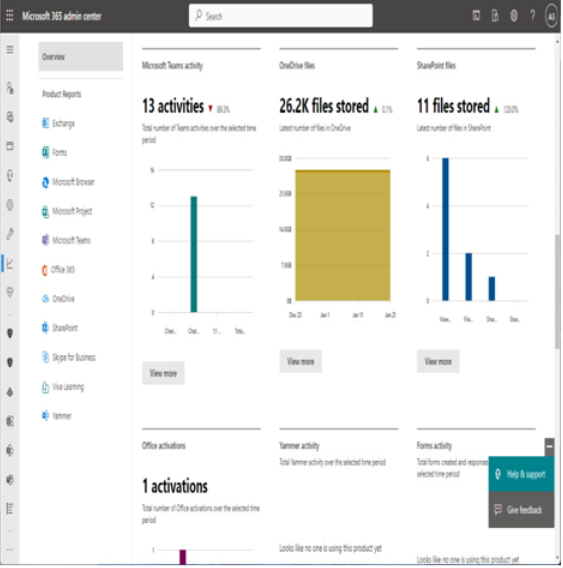
Figure 2.21 – Microsoft 365 usage reports
Usage reports can be accessed by navigating to the Microsoft 365 admin center (https://admin.microsoft.com), expanding Reports, and selecting Usage.
Viva Insights
Formerly known as Workplace Analytics, Viva Insights provides recommendations about personal and teamwork habits. Viva Insights has four core areas:
- Personal insights
- Teamwork habits
- Organization trends
- Advanced insights
Each of these areas has unique features that are part of the Viva story.
Personal insights
As the name suggests, personal insights are tailored to an individual. Personal insights are private and are only visible to the individual for whom they are intended. Personal insights are best viewed using the Viva Insights app in Microsoft Teams, as shown in Figure 2.22:
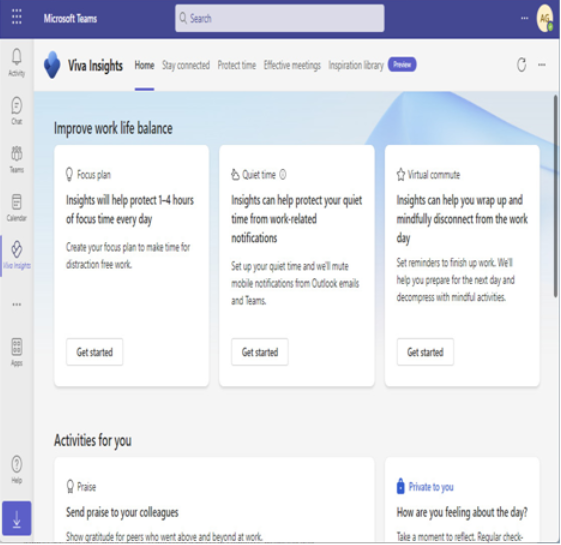
Figure 2.22 – Viva Insights app in Microsoft Teams
The Viva Insights app has functions to allow you to make a focus plan (sometimes referred to as the protect time feature), send praise to your colleagues either publicly or privately, and stay connected through AI-based task suggestions and meeting assistance.
The Viva Insights app also features Headspace guided meditation and mindfulness exercises, as well as prompts for taking a break and reflecting on your personal feelings. Using the Reflection activity card, you can even set daily reminders to check in on yourself:
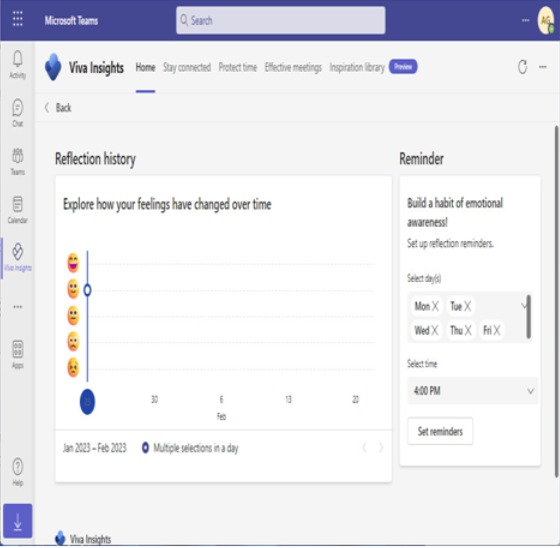
Figure 2.23 – Reflection activity card
Viva Insights also has a daily ramp-up and wind-down micro-app called Virtual commute, which lets users review upcoming meetings and tasks, block focus time, and initiate a variety of mini-break, meditative, and reflective activities. See Figure 2.23:
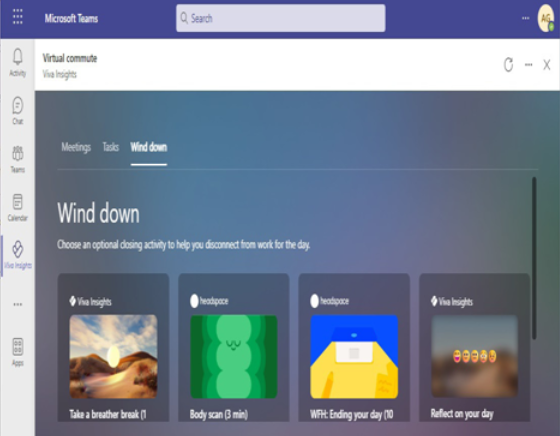
Figure 2.24 – Virtual commute activity card
Together, these insights features can help users manage both their productivity and personal well-being.