Label policies are on the client side and work inside applications such as Outlook and Word and in the web user interfaces for SharePoint, OneDrive for Business, and Power BI. Label policies can be made available to users via administrative units or to individual users and groups. Additionally, label policies can be made mandatory—that is, users are required to choose from the published labels to apply to content in the Office apps, documents, meetings, and Power BI content.
The wizard to publish label policies can be activated after a label has been created, or separately.
In the following example, you’ll look at creating a label policy for an existing label:
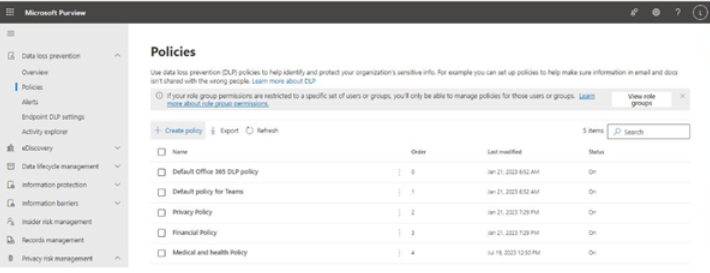
- In the Microsoft Purview compliance portal (https://compliance.microsoft.com), expand Information protection and select Label policies.
- Click Publish label, as shown in Figure 10.46:
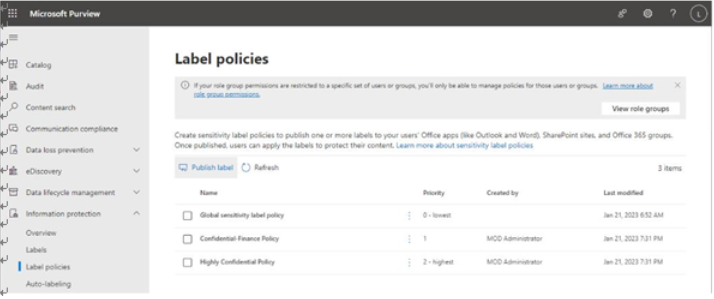
Figure 10.46 – Publishing a label
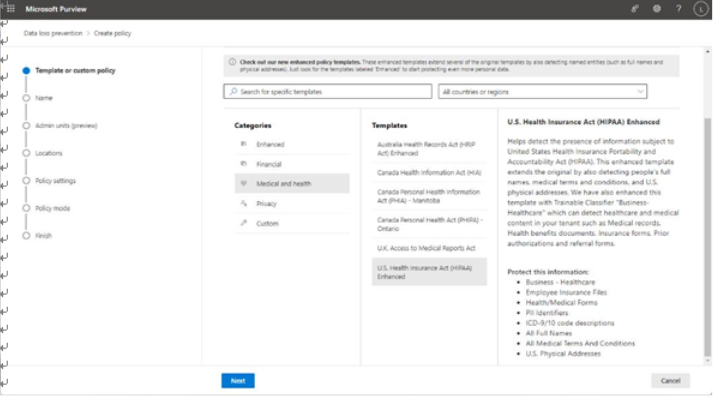
- On the Labels to publish page, as shown in Figure 10.47, click Choose sensitivity labels to publish and then select the labels to publish from the list. Click Add to add the labels to the list of labels that will be published as part of the policy. Click Next to continue.
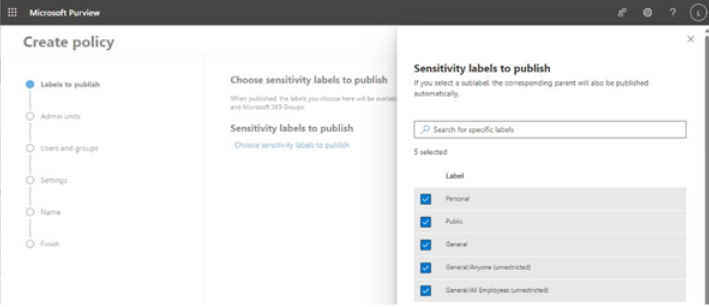
Figure 10.47 – Selecting labels to publish
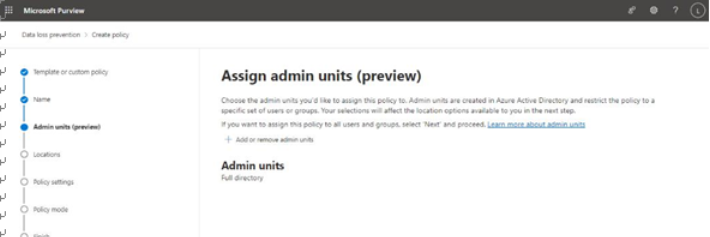
- On the Admin units page, choose which administrative units to use for scoping the policy. By default, the entire tenant is selected. Click Next.
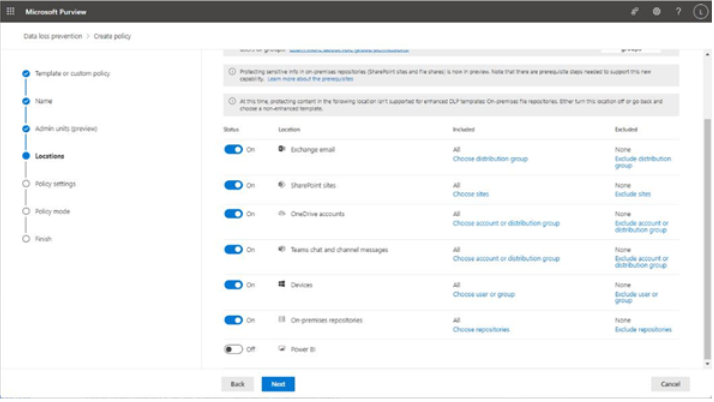
- On the Users and groups page, select which users or groups will receive the label policy. By default, all users and groups are included. Click Next.
- On the Settings page, choose the appropriate settings to apply to this policy. You can choose from Users must provide a justification to remove a label or lower its classification, Require users to apply a label to their emails and documents, Require users to apply a label to their Power BI content, and Provide users with a link to a custom help page. Click Next.
The Users must provide a justification to remove a label or lower its classification option has no additional configuration options, but users will have to enter classification text (which will be logged) when changing the label. Lowering a classification corresponds to its priority on the Label policies page.
The Provide users with a link to a custom help page option has only a single configuration field—a URL—which must be specified on this page.
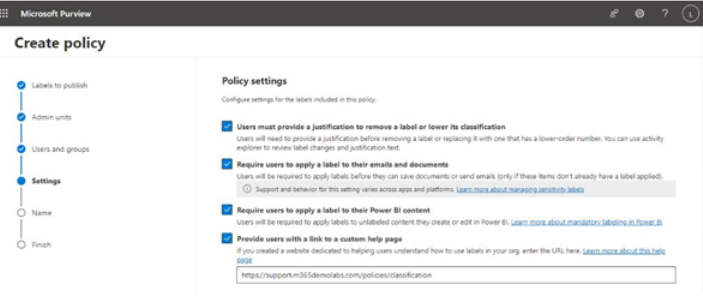
Figure 10.48 – Configuring policy settings
- On the Documents page, if you want to specify a default label, select it from the list of labels. The default label will be applied to the label automatically, though the user can select a different label from their available labels if the sensitivity of the content warrants a change. Click Next.
- On the Emails page, select Default label (you can choose Same as document) to choose the same label as you selected on the Documents page or one of the other available labels. It’s recommended to choose the Same as document label to help users avoid confusion and ensure consistency. If you selected Require users to apply a label to their emails and documents on the Settings page, you can choose Require users to apply a label to their emails on this page. You can also choose the Email inherits highest priority label from attachments option if you want an attachment’s assigned label to be able to potentially override an email label’s priority.
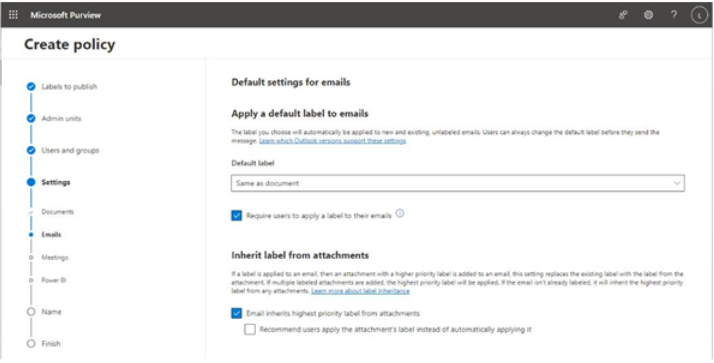
Figure 10.49 – Configuring email settings
- Click Next.
- If your organization requires labeling of all items (including calendar items), you have options for managing label application on the Apply a default label to meetings and calendar events page. You can choose a default label as well as the Require users to apply a label to their meetings and calendar events option (if the Require… checkbox was selected on the Settings page). If you don’t have a reason to require labeling of calendar invitations, leave the setting cleared. Click Next.
- On the Power BI page, you can choose a default label that will be applied to Power BI content. Organizations that have mandatory classification requirements should configure this option to help ensure compliance. For the exercise, select one of the labels that you have configured and click Next.
- On the Name page, enter a Name value for the label policy. Click Next.
- On the Finish page (depicted in Figure 10.50), review the settings and click Edit to change them if necessary, or click Submit to finish creating the policy.
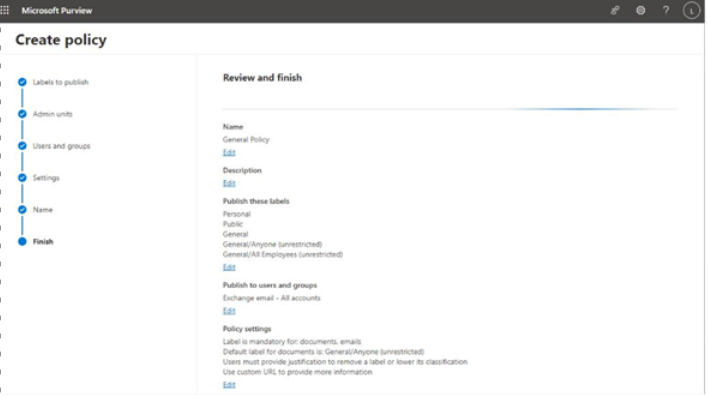
Figure 10.50 – Reviewing the final settings
After you’ve configured the label publishing policy, the labels will show up for use in application and user interfaces.