Application audit logs are useful for reviewing actions that have occurred in your tenant. You can view these audit logs from the Enterprise applications page in the Azure portal, as shown in Figure 2.13:
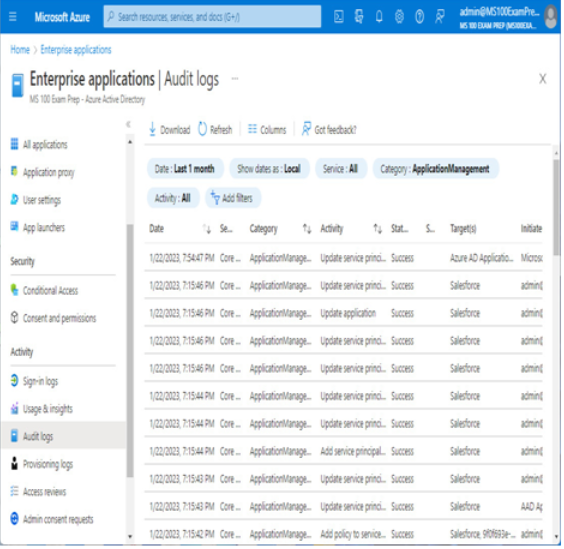
Figure 2.13 – Enterprise application audit logs
These audit logs show data regarding the service principal, applications, and type of action performed. You can select an individual audit item to view additional details. You can also perform filtering on several fields such as Status (Success or Failure), Initiated by (actor) (user or security principal that executed the action), User agent (device type or browser where the action was submitted), and Target (application or service that was affected).
You can also select an individual application (Enterprise applications | All applications) and view all of the audit logs that pertain specifically to that application.
Reviewing the sign-ins report
The sign-ins report shows data related specifically to sign-ins. Like the audit log data, you can view it across all applications (from the Enterprise applications | Audit logs page) or just for an individual application, as shown in Figure 2.14:
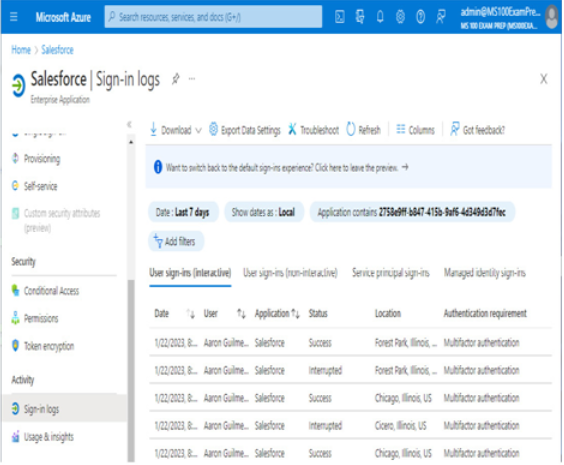
Figure 2.14 – Application sign-in logs
The application sign-in logs are useful for identifying potentially anomalous or malicious behavior. For example, if you see several failures for a particular user and they have a multifactor authentication requirement configured, the user may have a compromised password. If you see several failures for different users that are related to the same application, you may have an identity provisioning or single sign-on problem that needs to be addressed.
Sending activity log data to Azure Monitor
Azure Monitor is an additional subscription service that can be used to store and analyze logging and auditing data from a variety of sources, including Azure Active Directory, virtual machines, and applications. By connecting Azure AD data to Azure Monitor, you can enable Microsoft Defender to gain access to this data so that you can compare it against security logs, thereby improving risk management:
- From the Azure portal (https://portal.azure.com), enter Log Analytics workspaces in the search box.
- Click Create.
- From the Subscription drop-down menu, select an Azure subscription.
- From the Resource group drop-down menu, select an existing resource group or click Create new to create a new one.
- Enter a new workspace Name and select a Region option for where you want to provision the workspace.
- Click Review + Create.
- Click Create.
Once the workspace has been provisioned, you can connect the activity log to Azure Monitor.