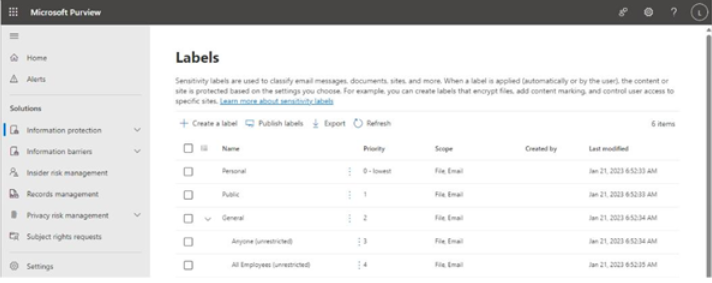
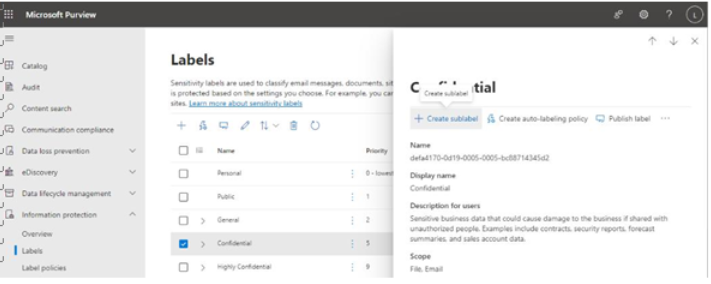
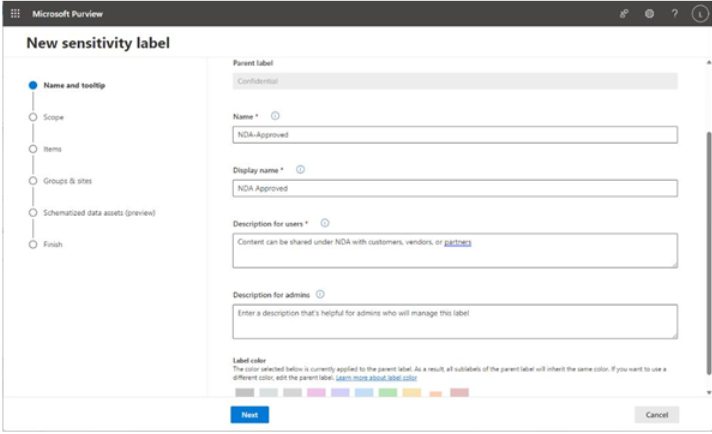
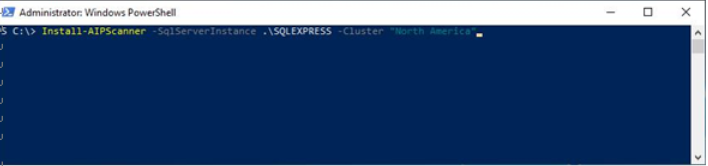
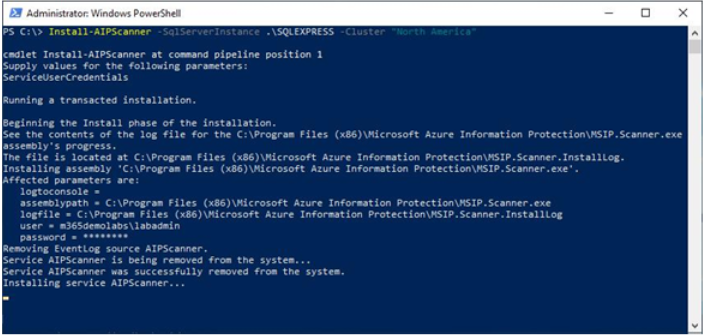
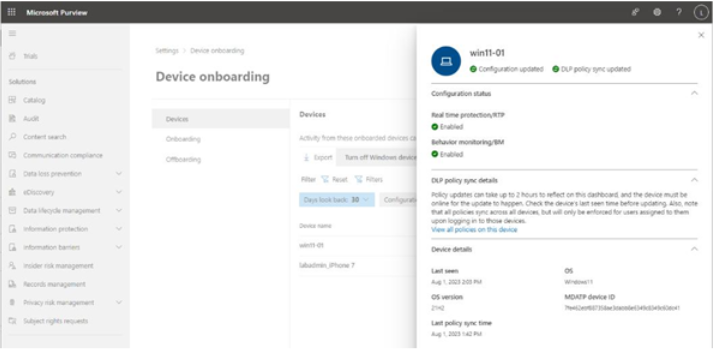
Activity explorer is a dashboard-style interface that displays charts for the various compliance activities in Microsoft 365, including file deletions, archive creations, label applications, DLP rule matches, and content classification.
Figure 11.30 depicts the default view of the dashboard with the Activity dropdown selected to show the filter options:
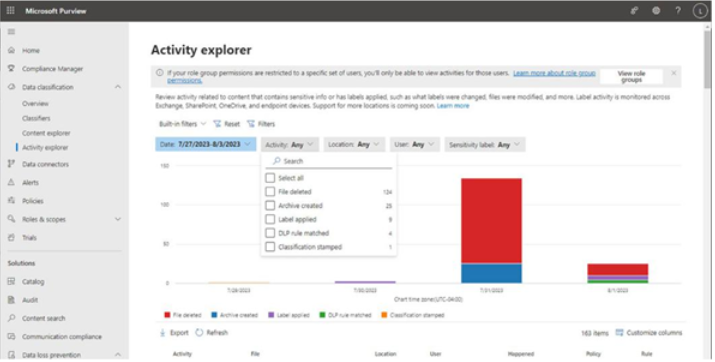
Figure 11.30 – Activity explorer dashboard
You can use the filters to locate and display only the data that matches your criteria. Once you have identified the type of data to display, you can select an individual event to view the details surrounding it, as shown in Figure 11.31:
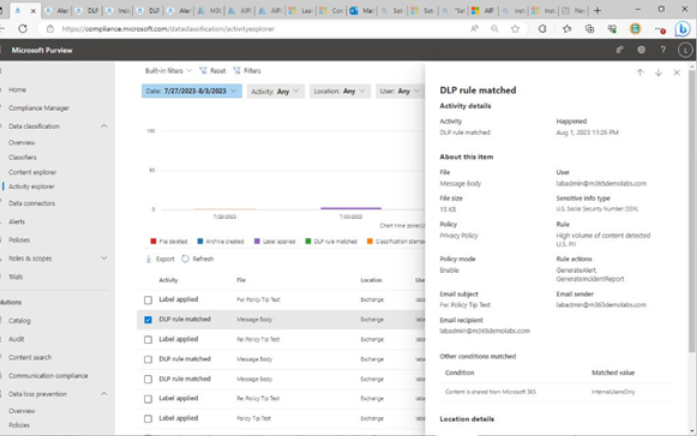
Figure 11.31 – Viewing details of an event in Activity explorer
Activity explorer, whether it is the Activity explorer node under Data classification or under Data loss prevention, shows exactly the same data and events. Some activity details may direct you to individual devices or other items in the Microsoft 365 Defender portal. DLP activities are not typically linked to other pages, however.
Microsoft 365 Defender Alerts Dashboard
The Microsoft 365 DefenderAlerts dashboard displays security-related alerts generated throughout your Microsoft 365 tenant. SeeFigure 11.32:
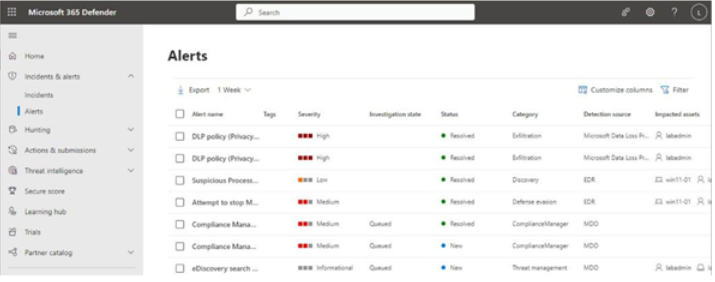
Figure 11.32 – Microsoft 365 Defender Alerts dashboard
The Alerts dashboard shows the current status of alerts as well as information about the category of the alert, where the alert originated, its severity, and its impacted assets. In the case of DLP alerts, the detection source is Microsoft DataLoss Prevention.
Selecting the row of an event brings up a details flyout, providing information regarding the alert’s source and classification. See Figure 11.33:
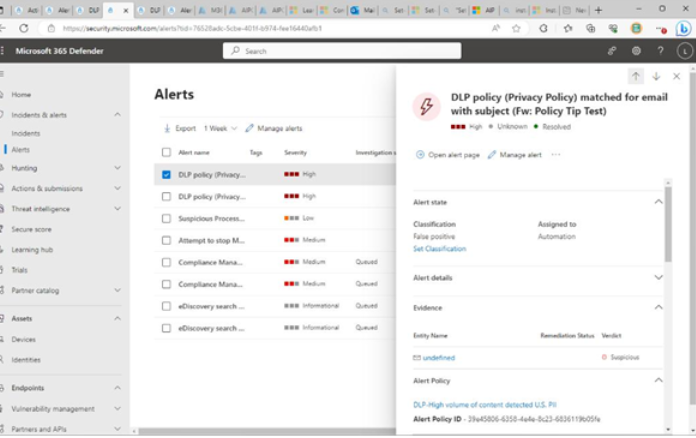
Figure 11.33 – Alert detail flyout
From this flyout, you can select Open alert page to view the overall alert and the alert story, Manage alert to update its status, or the ellipsis (…) for the additional options Link alert to another incident and Ask Defender Experts.
Like the compliance portal’s Alerts and Activity explorer views, there aren’t remediation tasks that can be performed on these pages.
Microsoft 365 Defender Incidents Dashboard
From the perspective of responding to alerts, the Microsoft 365 DefenderIncidents dashboard gives you the most capability, as shown in Figure 11.34:
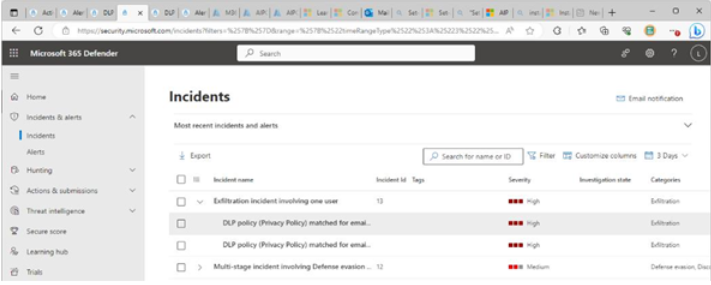
Figure 11.34 – Microsoft 365 Defender Incidents dashboard
While the other dashboards only highlight activity and events, the Incidents dashboard allows you to see the most detail and the context of the alert inside the incident’s attack story. By selecting an incident, you can review the attack story (chain of related events) as well as the corresponding alerts and assets involved.
In this DLP example, the user sent a file with sensitive information. It could have been accidental or intentional, or it could also have represented a malicious actor who has gained control of the user’s account and is attempting to exfiltrate data.
By selecting the Assets tab in an incident, for example, you can locate the impacted user and choose to perform activities against that user such as requiring the user to sign in again, suspending the account, or confirming the identity as compromised. See Figure 11.35:
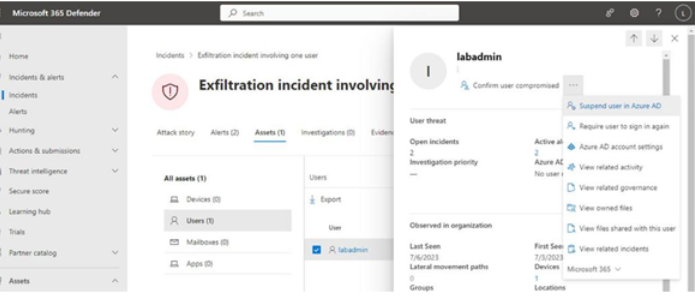
Figure 11.35 – Viewing the user actions in a DLP incident
By selecting the Evidence tab of the incident and then selecting an item inside it, you may be presented with the Go hunt option. This will create a hunting query targeting this item to help you locate it in the organization. See Figure 11.36:
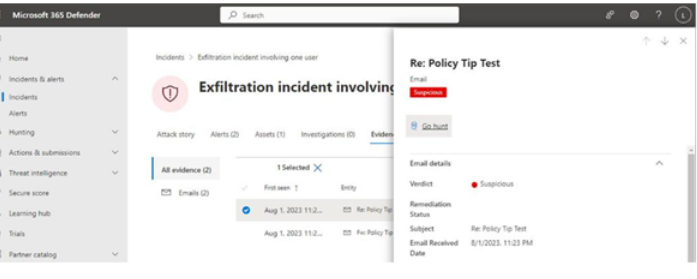
Figure 11.36 – Microsoft 365 Defender incident evidence
Selecting Run query on the Advanced hunting window will take the pre-loaded query and return corresponding results. See Figure 11.37:
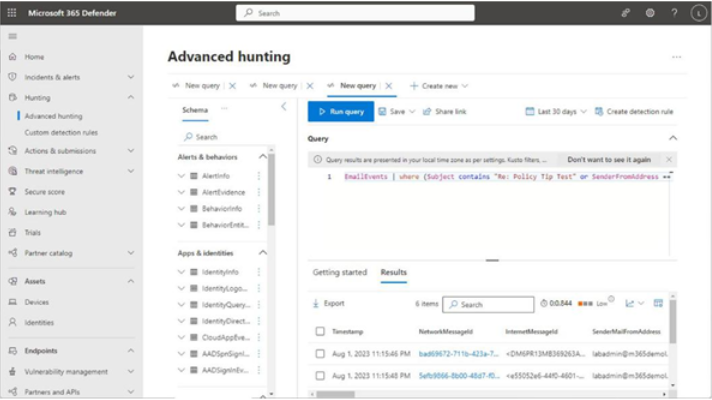
Figure 11.37 – Advanced hunting results
Selecting the hyperlinked value in the NetworkMessageId column (shown in Figure 11.37) will display details of the actual item (Figure 11.38). From there, you can perform remediation tasks.
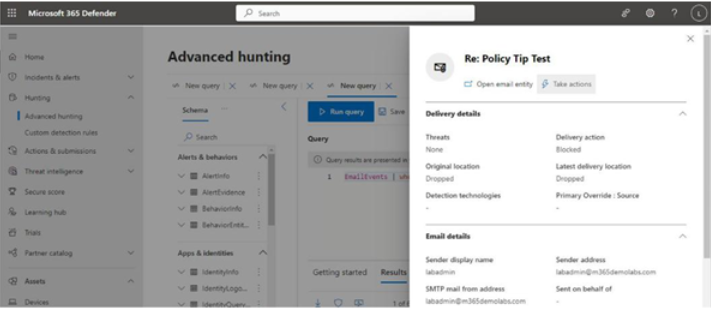
Figure 11.38: Advanced hunting item details
By selecting Take action, as shown in Figure 11.38, you can initiate a variety of triage and response tasks to help mitigate or resolve the issue. Depending on the data type and risk, you may want to move the item or delete it altogether. You can use the message details to create additional rules for restricting content as well.
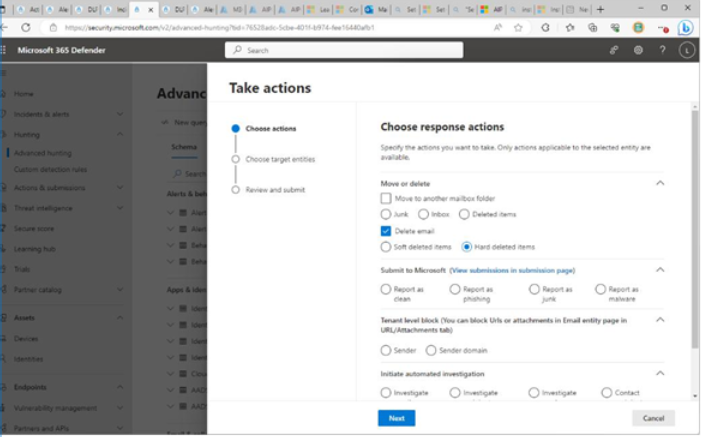
Figure 11.39 – Initiating remediation tasks
Additional remediation options from this page include launching an investigation or contacting the user.