Once you’ve got the AIP UL client deployed, the scanner settings configured, and the app registration details, you can begin installing scanner cluster nodes in your on-premises environment. You’ll need the name of the scanner cluster that you created in the Microsoft Purview compliance portal to complete this task, as well as a service account that will be used to run the local service.
To install and configure the scanner service, follow these steps:
- On a server that you wish to use to deploy the scanner, launch an elevated PowerShell session.
- From the elevated prompt, run the following command:
Install-AIPScanner -SQLServerInstanceName -Cluster
For example, if you deployed a local SQLExpress database instance and are using a scanner cluster called North America, you could enter the following:
Install-AIPScanner -SQLServerInstanceName .\SQLExpress -Cluster “North America” See Figure 11.19:
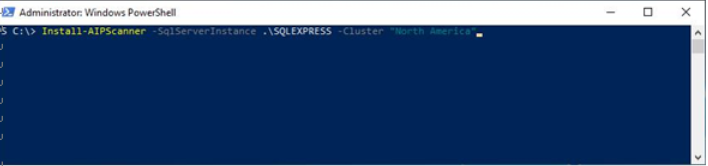
Figure 11.19 – Starting the AIP scanner installation
- When prompted, enter the service account credential that will be used.
- Wait for the configuration to be completed.
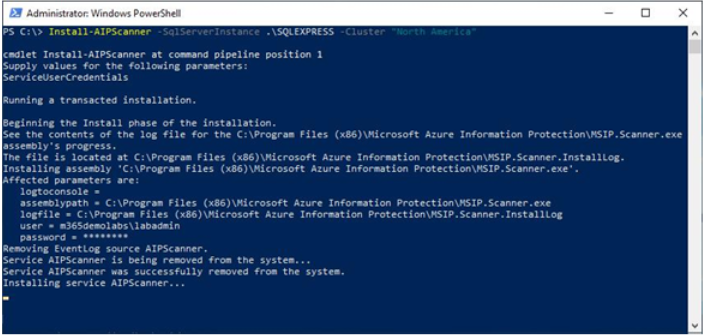
Figure 11.20 – Installing the AIP scanner
- In the elevated PowerShell console on the server where the AIP scanner was installed, run the following command:
Set-AIPAuthentication -AppID -AppSecret -TenantId -DelegatedUser [email protected]
Once the scanner has been registered with the cluster, the content scan you configured will start. You can then use the on-premises repository location as part of a DLP policy.
Next, you’ll shift to managing Endpoint DLP.
Implementing Endpoint DLP
To this point, you’ve been working with managing DLP capabilities for content that is stored in the Microsoft 365 service or moving across the Microsoft 365 ecosystem—through applications such as Exchange Online and SharePoint Online.
But what if the data is created or stored on an endpoint device? Can organizations use the same types of DLP technology to protect and alert on activities with that data?
Yes! Microsoft’s Endpoint DLP can do exactly this!
Some of the features of Endpoint DLP include the following:
• Restricting application access to sensitive data
• Automatically quarantining content being accessed from restricted apps
• Preventing protected files from being transferred via Bluetooth
• Preventing certain browsers from accessing protected content
• Preventing browsers from uploading to restricted domains
• Restricting the transfer of protected content to USB storage devices
• Restricting printing
Many organizations—especially those that deal with confidential information—need to be able to protect data against unauthorized storage and use. Endpoint DLP is a great solution to help achieve that.
Further Reading
For a complete list of monitored activities, see https://learn.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-learn-about?view=o365-worldwide#endpoint-activities-you-can-monitor-and-take-action-on.
• In addition to preventing certain types of activities, endpoint DLP also monitors activities across a wide variety of files on both Windows and macOS platforms. Out of the box, endpoint DLP monitors documents (.doc, .docx, etc.), spreadsheets (.xls, .xlsx, etc.), archive files (.zip, .tr, etc.), and presentations (.ppt, .pptx, etc.), regardless of whether a policy is configured to monitor or act on them. Endpoint DLP can even be integrated with Azure Optical Character Recognition (OCR) to scan PDF images, JPGs, and other image files.
What’s in a Name?
Endpoint DLP supports documents and files based on their Multipurpose Internet Mail Extension (MIME) type, so changing a file’s extension name won’t affect whether Endpoint DLP is able to capture audit log data or enforce a policy against it.
Endpoint DLP has two requirements: a supported operating system and a supported subscription. Endpoint DLP can be enabled for Windows 10, Windows 11, and macOS 10.5 or later devices and requires one of the following subscriptions:
• Microsoft 365 E5/A5/G5
• Microsoft 365 E5/A5/F5/G5 Compliance and F5 Security & Compliance
• Microsoft 365 E5/A5/F5/G5 Information Protection & Governance
With those requirements out of the way, let’s go through the onboarding process.
Since endpoint DLP builds on the Microsoft Defender for Endpoint(MDE) product, it can be onboarded using a variety of methods (Intune, Group Policy, Configuration Manager, and scripts). Microsoft’s best practice for organizations using the entire Microsoft 365 suite is to use Intune to deploy and configure policies.
Note
If using Intune to deploy endpoint DLP, the devices must be Intune enrolled.
If you’ve already got MDE onboarded, the next step is to onboard the devices into the Microsoft Purview compliance portal. To configure onboarding through Purview, follow these steps:
- Navigate to the Microsoft Purview compliance portal (https://compliance.microsoft. com) and select Settings | Device onboarding. See Figure 11.21:
Figure 11.21 – Device onboarding
- In the middle pane, select Devices and then select Turn on device onboarding in the main window.
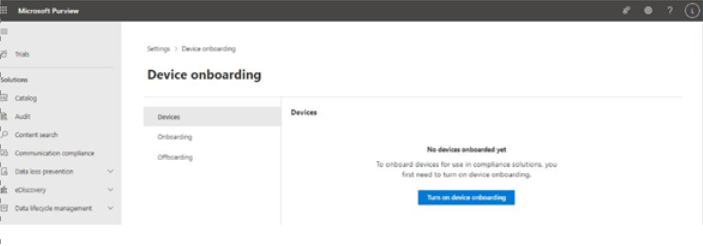
Figure 11.22 – Turning on device onboarding
- Acknowledge the prompt that existing MDE devices will be automatically onboarded by clicking OK.
- Click OK to acknowledge that device monitoring has been turned on.
That’s it! That’s all it takes. You can view the status for devices on the Devices tab of the Device onboarding page, as shown in Figure 11.23:
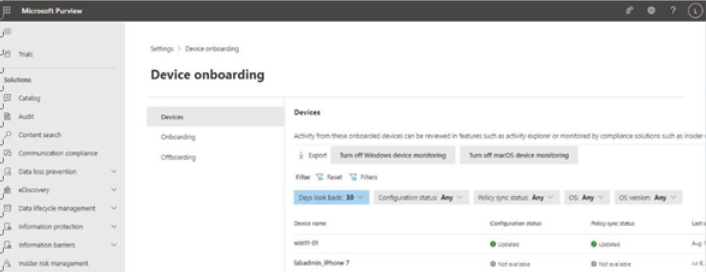
Figure 11.23 – List of onboarded devices
The Configuration status column will show that the device has received the updated onboarding configuration. The Policy sync status column will show whether DLP policies have been synchronized to the device.
The policy sync status can take up to two hours to show up, so you may need to be patient. You can attempt to trigger the policy application to come down sooner using the Resync button in the Intune management portal (Devices | Windows devices or macOS devices | Overview) or by restarting the device itself.
After the policy refresh cycle has completed, when you select an onboarded device from the Settings | Device onboarding | Devices page, you can see which device DLP policies have been synchronized, as shown in Figure 11.24:
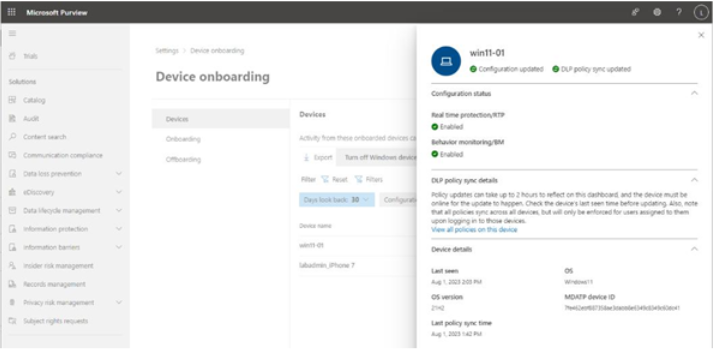
Figure 11.24 – Viewing synchronized DLP policies
Next, you’ll look at working with DLP alerts.